Canary Infrastructure vs. Real World TTPs
Effective cloud security focuses on the techniques used by threat actors in real world incidents. I maintain aws-customer-security-incidents to consolidate public data on these incidents and actors.
Canaries generally, and canary infrastructure specifically, are an elegant approach to alert with confidence on actions that:
- Should never happen during the normal course of business, and
- Attackers can’t resist taking
Tracebit outlines the benefits in greater depth, but the basic idea is to seed your cloud environment with tripwires that trigger high signal alerts based on common attacker TTPs.
Let’s look at three recent (sophisticated) AWS security incidents, and talk about how canaries could help you detect these early, and throughout the attack lifecycle.
Ransomware Attack
The first case comes from Yotam Meitar, who shared the details in his talk at fwd:cloudsec 2024: “Responding to Sophisticated Ransom Attacks in the Cloud: A Real-World Case Study”
In this incident, an engineer had deployed a known-vulnerable application to an EKS Pod. This application was intended for testing and only exposed internally, but was deployed to production. A second employee accidentally changed the shared Security Group that managed access to that application, and left it publicly accessible.
An attacker quickly discovered the exposed vulnerability during an untargeted scan. They compromised the Kubernetes Pod, which allowed them to assume the EC2 Instance IAM Role. This role had over-privileged access to Secrets Manager. One accessible secret granted the ability to bypass a custom Identity Provider that was in use. Finally, with access from the Identity Provider, the attacker was able to exfiltrate MongoDB backups from an S3 bucket.
From initial access, this attack only took a couple of days. The victim organization became aware upon receiving the ransom note. Yotam makes it clear that this speed is common in cloud incidents.
Detecting this attack with Tracebit

This attack was “fast,” but canaries are faster. In this case, we can see several opportunities for canary infrastructure to provide an early warning of the attack.
- Instance compromise: the attackers initial foothold was a compromised application running in EKS. Canary Credentials can be placed in multiple common locations, accessible to the application and EKS Pod, including environment variables and well-known `.aws/` configuration files. In such untargeted attacks, attackers commonly search for and use credentials in these locations.
- Secrets Manager: the attackers proceeded to use the instance’s IAM role to access secrets in Secrets Manager. Tracebit supports creating canary Secrets Manager secrets, tailored to your environment.
- Identity Provider: The custom identity provider was unique to this victim. However, it could be used with the very flexible Canary Credentials as a way to detect bypass or compromise of such a critical service. If the victim were using Okta, Tracebit can go a step further with native support for canaried Okta Applications.
- S3: The access to and exfiltration of data from S3 offers a final opportunity to catch the attacker using canaried S3 infrastructure. Ideally, you can catch attackers well before they start to exfiltrate data. However, as I found in my Guardduty research, you should layer in canaries to ensure reliable, deterministic detection.
SugarCRM
Unit42’s Margaret Zimmermann shared details on incidents related to a SugarCRM remote code vulnerability (CVE-2023-22952) at Black Hat, and in a blog post.
In one case, SugarCRM was being run on EC2. An attacker gained initial access via the aforementioned vulnerability. The attacker was then able to grab long term access keys from the plaintext credentials file on the host. Once they had these credentials, they used their access to perform discovery calls against the AWS control plane. This discovery activity included GetCallerIdentity, AWS Organizations, and Cost & Usage. In addition, the attacker ran both Pacu and ScoutSuite to scan a broad set of AWS services. The attacker moved on to exploitation and exfiltration, targeting RDS. The attacker was able to create a snapshot of the RDS instance, exposed it on port 3306, and restore the snapshot in an attacker controlled account.
Overall, these attacks occurred over a few weeks, with the AWS component spanning a few days. Unit42 observed that the discovery phases appeared quick and automated, but exfiltration was slower and clearly hands-on-keyboard based on observed typos.
Detecting this attack with Tracebit
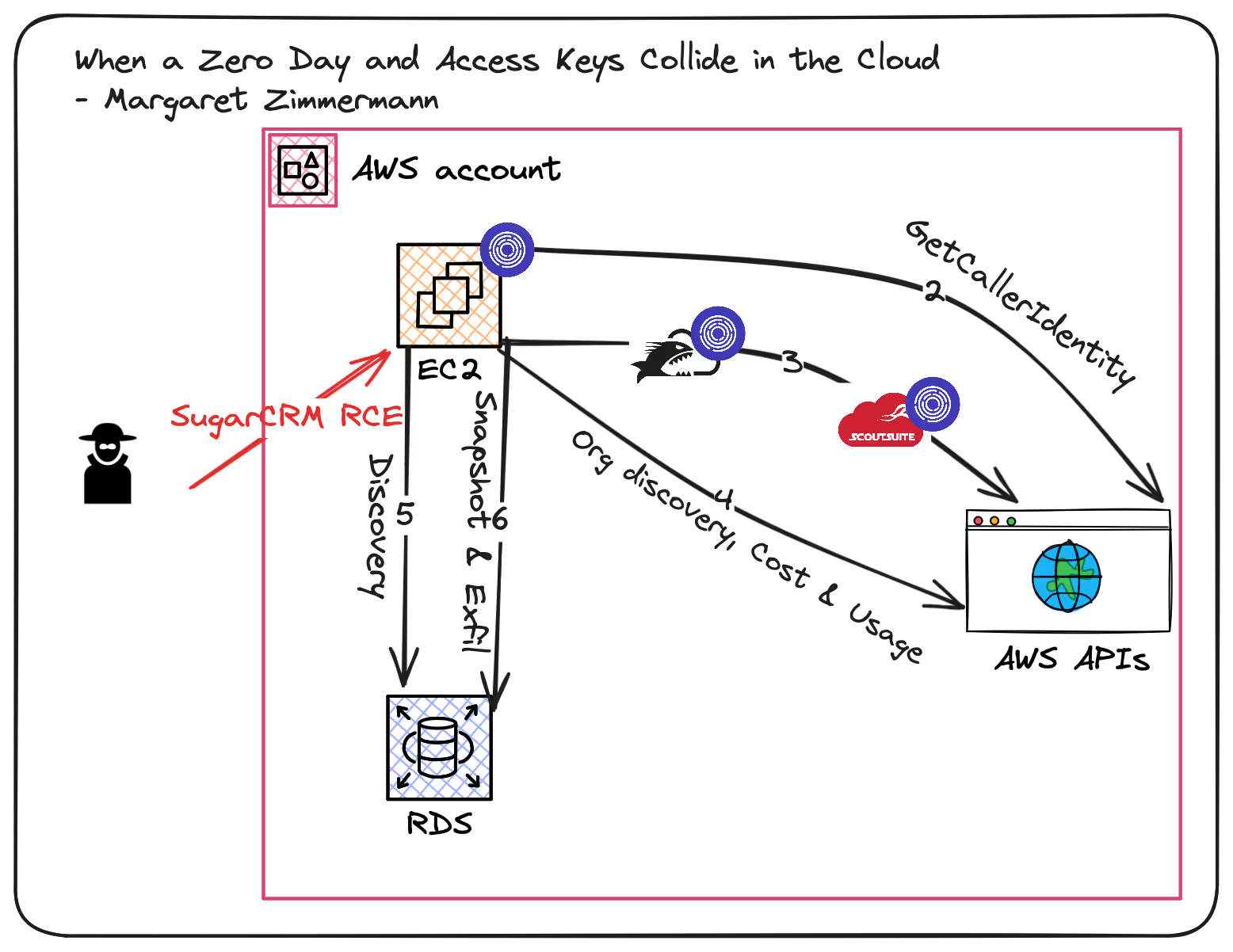
While this attack chain was significantly less involved than the Ransomware case, it presents numerous canary infrastructure detection opportunities.
- Instance compromise: the attackers initial foothold was a compromised application running on an EC2 instance. In this case, they found valid credentials in the `.aws/` configuration files. However, canary credentials could still be placed alongside these valid credentials, or even better could be implemented in parallel to a move to using more secure instance roles (with IMDSv2).
- Noisy Discovery: this attack took a scattershot approach to discovery, including running Pacu and ScoutSuite. Canary Infrastructure throughout the environment would quickly signal this level of broad enumeration. The false positive noise of security tools can drown out this signal, which is why Tracebit has been designed to automatically filter out your existing security tools. Pacu has modules that would trip on a variety of canary resources, such as Tracebit’s SSM Parameters and DynamoDB tables. ScoutSuite’s IAM and S3 enumeration are other opportunities for canary detection.
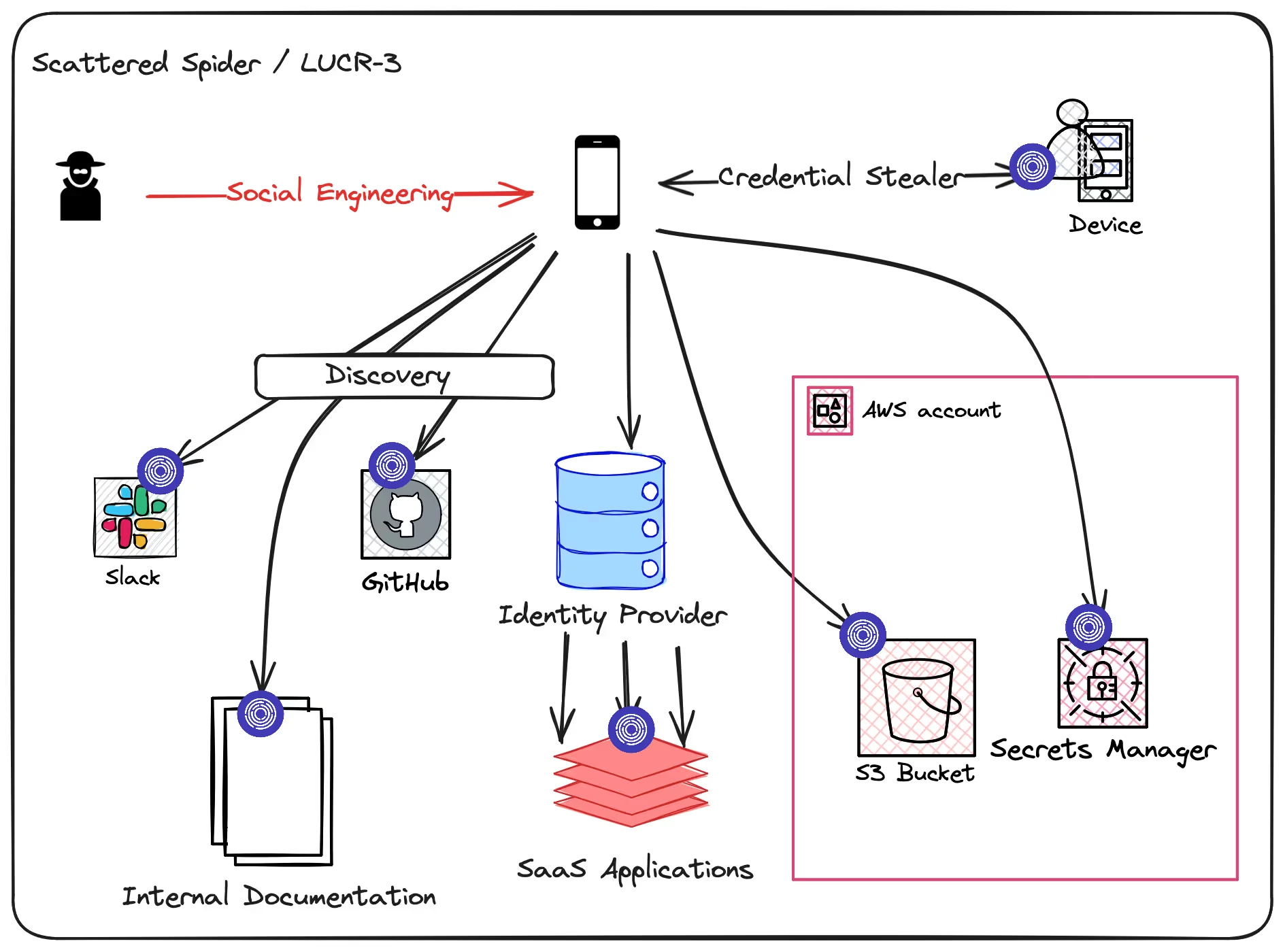
Scattered Spider / LUCR-3 / UNC3944 / Star Fraud / Octo Tempest / Scatter Swine / Muddled Libra
Scattered Spider is perhaps the most prolific and well covered threat actor that targets cloud environments. Reports on the group have been produced by, among others:
- CISA - Scattered Spider
- Mandiant - Why Are You Texting Me? UNC3944 Leverages SMS Phishing Campaigns for SIM Swapping, Ransomware, Extortion, and Notoriety
- Reliaquest - Scattered Spider Attack Analysis
- Crowdstrike - Not a SIMulation: CrowdStrike Investigations Reveal Intrusion Campaign Targeting Telco and BPO Companies
- Unit42 - Muddled Libra’s Evolution to the Cloud
- Permiso - LUCR-3: Scattered Spider Getting SaaS-y in the Cloud
There is no single case to cover here, but we can consolidate a “standard” Scattered Spider cloud attack chain from the details in these reports.
Scattered Spider generally starts with targeted Social Engineering, which can also involve phishing, smishing, SIM swapping and MFA fatigue tactics. After initial access is achieved, they:
- Search internal documentation, chat logs, and code, primarily targeting credentials
- Deploy malware for credential theft and search for insecurely stored credentials on victim’s systems
- Access Identity Provider (Okta) dashboards and use connected applications and CSP environments
- Enumerate sensitive AWS services, including AWS S3 and Secrets Manager
After they’ve compromised sufficient data, Scattered Spider seeks financial gain through some combination of exfiltration, extortion, and ransomware deployment.
Detecting this attack with Tracebit

The breadth of discovery Scattered Spider demonstrates, paired with their focus on cloud resources and Identity Providers, leaves them vulnerable to early detection by Canary Infrastructure.
- Noisy Discovery: this threat actor’s tendency to search internal chat logs, documentation, and code repositories all offer opportunities to seed canary credentials.
- Credential Stealing Malware: especially if you’re not using static credentials, deploying canary credentials across your employee laptops can tempt attackers into early detection.
- Identity Provider: Tracebit’s native Okta canaries are perfectly positioned to catch this actor’s pattern of pivoting through employee IdP dashboards and into connected applications
- S3 & Secrets Manager: The access to and exfiltration of data from S3 offers a final opportunity to catch the attacker, using canaried S3 infrastructure and canaried data within S3 buckets. Similarly, Tracebit’s canary Secrets Manager secrets, tailored to your environment, are an appealing lure for LUCR-3
Takeaways
There is a common saying that “At the speed of cloud, detection is way too late.”
I find that defeatist. While we’re commonly told cloud attacks are heavily automated and occur rapidly, these cases show that even sophisticated actors can take days to achieve their goals.
Looking just at this small sample of attacks, we can also see the diversity in attacker techniques. Some implicate EC2 instances, or EKS. Some attackers target S3, others Secrets Manager, or RDS. We see custom IdPs compromised, as well as SaaS IdPs.
Canary Infrastructure offers both flexible and targeted detection opportunities against these attacks. Canary credentials are an example of a portable tripwire, that can detect everything from credential stealing malware to instance compromise. On the other hand, Tracebit’s native Okta Canaries offer a uniquely camouflaged answer to Scattered Spider’s focus on IdPs.
If you'd like to learn more about how Tracebit can level up your detections - click Book a demo above to schedule a call with one of the founders.
With thanks to:
“Phone” by Joris Hoogendoorn, from Noun Project (CCBY3.0)
“Intruder” by Chaiconator, from Noun Project (CCBY3.0)